https://blog.secarclabs.com/post/dfir-series-windows-defender-tamper-protection
Windows Defender Tamper Protection is a security feature to enhance the protection provided by Windows Defender Antivirus. Tamper Protection is designed to prevent malicious actors or unauthorized programs from modifying or disabling key security settings in Windows Defender.
When Tamper Protection is enabled, it helps safeguard critical Windows Defender features, including real-time protection, cloud-based protection, behavior monitoring, and more. It prevents unauthorized changes to these security components, ensuring that they remain active and effective in defending your system against malware and other threats.
Tamper protection is available for devices that are running one of the following versions of Windows:
- Windows 10 and 11 (including Enterprise multi-session)
- Windows Server 2022, Windows Server 2019, and Windows Server, version 1803 or later
- Windows Server 2016 and Windows Server 2012 R2 (using the modern, unified solution)
*For Windows Server 2012 R2, 2016, or Windows version 1709, 1803, or 1809, Tamper Protection would not appear in the Windows Security app. Instead, you can use PowerShell to determine whether tamper protection is enabled.
Effects of tamper protection
Based on the Microsoft Documentation from What happens when tamper protection is turned on?, the following behaviors would be available when tamper protection is turned on.
- Virus and threat protection remains enabled.
- Real-time protection remains turned on.
- Behavior monitoring remains turned on.
- Antivirus protection, including IOfficeAntivirus (IOAV) remains enabled.
- Cloud protection remains enabled.
- Security intelligence updates occur.
- Automatic actions are taken on detected threats.
- Notifications are visible in the Windows Security app on Windows devices.
- Archived files are scanned.
Check Tamper Protection Status
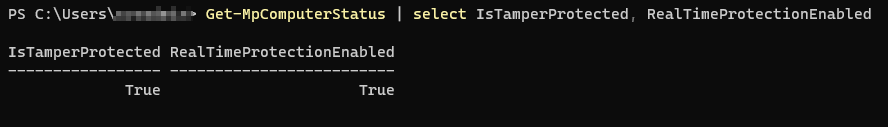
Configure/Manage tamper protection
The options on how to configure/manage tamper protection are listed below(How do I configure or manage tamper protection?):
| Method | What you can do |
|---|---|
| Use the Microsoft 365 Defender portal. | Turn tamper protection on (or off), tenant wide. See Manage tamper protection for your organization using Microsoft 365 Defender.This method won’t override settings that are managed in Microsoft Intune or Configuration Manager with tenant attach. |
| Use the Microsoft Intune admin center. | Turn tamper protection on (or off), tenant wide, or apply tamper protection to some users/devices. You can exclude certain devices from tamper protection. See Manage tamper protection for your organization using Intune.Protect Microsoft Defender Antivirus exclusions from tampering. See Tamper protection for antivirus exclusions. |
| Use Configuration Manager with tenant attach. | Turn tamper protection on (or off), tenant wide, or apply tamper protection to some users/devices. You can exclude certain devices from tamper protection. see Manage tamper protection for your organization using tenant attach with Configuration Manager, version 2006. |
| Use the Windows Security app. | Turn tamper protection on (or off) on an individual device that isn’t managed by a security team (such as devices for home use). See Manage tamper protection on an individual device.This method won’t override tamper protection settings that are managed by the Microsoft 365 Defender portal, Intune, or Configuration Manager, and it isn’t intended to be used by organizations. |
Detecting & Alerting on Tamper Protection
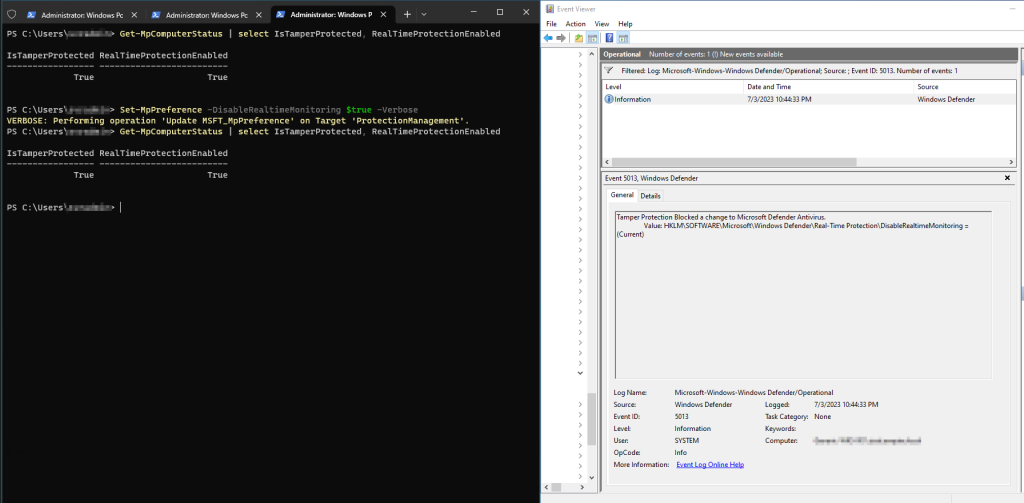
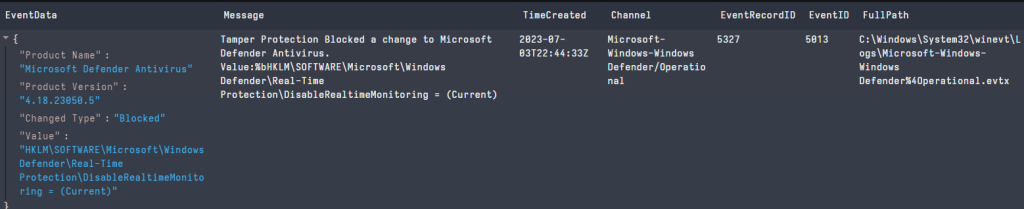
Whenever a tampering attempt is observed, for example like trying to disable Defender realtime monitoring with tamper protection enabled, a WEV log would be generated with the EID of 5013. If MDE is present, an alert is raised in the Microsoft 365 Defender portal (https://security.microsoft.com).
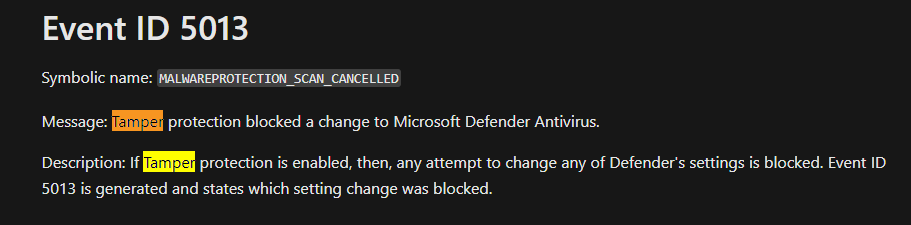
The images below shows Tamper Protection in action.
References:
Protect security settings with tamper protection | Microsoft Learn